If set to true , then during authentication with the bearer token, the adapter will verify whether the token contains this client name resource as an audience. The option is especially useful for services, which primarily serve requests authenticated by the bearer token. This is set to false by default, however for improved security, it is recommended to enable this. See Audience Support for more details about audience support.
You then have two options to secure your WARs. Both methods are described in this section. WildFly has built-in support for single sign-on for web applications deployed to the same WildFly instance. This should not be enabled when using Keycloak. This section describes how to secure a WAR directly by adding configuration and editing files within your WAR package. The first thing you must do is create a keycloak.
The format of this configuration file is described in the Java adapter configuration section. You also have to use standard servlet security to specify role-base constraints on your URLs.
You do not have to modify your WAR to secure it with Keycloak. Instead you can externally secure it via the Keycloak Adapter Subsystem. This metadata is instead defined within server configuration i. The secure-deployment name attribute identifies the WAR you want to secure. Its value is the module-name defined in web. The rest of the configuration corresponds pretty much one to one with the keycloak. It provides an example XML file you can cut and paste. If you have multiple deployments secured by the same realm you can share the realm configuration in a separate element.
For example:. To propagate the security context to the EJB tier you need to configure it to use the "keycloak" security domain.
JRebel changelog
This can be achieved with the SecurityDomain annotation:. For more information see the Red Hat Subscription Management documentation. If you are already subscribed to another JBoss EAP repository, you must unsubscribe from that repository first. Keycloak supports securing your web applications running inside JBoss Fuse 6.
Related Articles
Apache Camel Jetty endpoints running with the Camel Jetty component. Apache CXF endpoints running on their own separate Jetty engine. You must first install the Keycloak Karaf feature. Next you will need to perform the steps according to the type of application you want to secure. All referenced web applications require injecting the Keycloak Jetty authenticator into the underlying Jetty server.
The steps to achieve this depend on the application type. The details are described below.
JAX-RS @Path URIにマッチする例
The best place to start is look at Fuse demo bundled as part of Keycloak examples in directory fuse. Most of the steps should be understandable from testing and understanding the demo. You must first install the keycloak feature in the JBoss Fuse environment. The keycloak feature includes the Fuse adapter and all third-party dependencies.
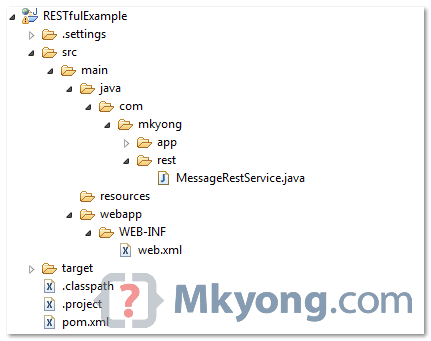
You can install it either from the Maven repository or from an archive. This is useful if you are offline or do not want to use Maven to obtain the JAR files and other artifacts.
HTTP Status - Could not find resource for r |JBoss Developer
Unzip it into the root directory of JBoss Fuse. The dependencies are then installed under the system directory. You can overwrite all existing jar files. Install the corresponding Jetty adapter. Since the artifacts are available directly in the JBoss Fuse system directory, you do not need to use the Maven repository. Add the jetty-web. The format of this configuration file is described in the Java Adapters Config section.
It is also possible to make this file available externally as described in Configuring the External Adapter. Ensure your WAR application imports org. MF file, under the Import-Package header. Using maven-bundle-plugin in your project properly generates OSGI headers in manifest. If you do not want the keycloak. That component uses keycloak. You can use this method if you have a servlet class inside your OSGI bundled project that is not deployed as a classic WAR application.
Fuse uses Pax Web Whiteboard Extender to deploy such servlets as web applications. Keycloak provides PaxWebIntegrationService, which allows injecting jetty-web. Note that your servlet needs to depend on it. An example configuration:. MF must contain at least these imports:. You can secure Apache Camel endpoints implemented with the camel-jetty component by adding securityHandler with KeycloakJettyAuthenticator and the proper security constraints injected.
Reply via email to
The roles, security constraint mappings, and Keycloak adapter configuration might differ slightly depending on your environment and needs. MF needs to contain these imports:. But you must still use specific implementation classes and provide instructions on how to integrate with Keycloak. The way to configure the integration mechanism depends on the Camel component for which you configure your RestDSL-defined routes.
The following example shows how to configure integration using the Jetty component, with references to some of the beans defined in previous Blueprint example. To run your CXF endpoints secured by Keycloak on separate Jetty engines, complete the following steps:. Some services automatically come with deployed servlets on startup. Securing such endpoints can be complicated.
- bc background criminal record checks!
- laws for birth certificates in ca!
- how to change name on birth certificate in california!
- RESTEasy JSON Example with Jackson!
One approach, which Keycloak is currently using, is ServletReregistrationService, which undeploys a built-in servlet at startup, enabling you to redeploy it on a context secured by Keycloak. For this reason, using your own Jetty engine for your applications as described in Secure CXF Application on separate Jetty Engine then gives you more control over security for each individual application. Note that you do not need the web. Keycloak mainly addresses use cases for authentication of web applications; however, if your other web services and applications are protected with Keycloak, protecting non-web administration services such as SSH with Keycloak credentials is a best pracrice.
In Keycloak create a client for example, ssh-jmx-admin-client , which will be used for SSH authentication. The easiest way is to install the keycloak-jaas feature, which has the JAAS realm predefined. For details see the JBoss Fuse documentation. Note that the user needs to have realm role admin to perform all operations or another role to perform a subset of operations for example, the viewer role that restricts the user to run only read-only Karaf commands.
Otherwise it might be better to use hawt. For more details see Hawtio Admin Console. Create a client in the Keycloak administration console in your realm. Create the keycloak-hawtio-client. Change the realm , resource , and auth-server-url properties according to your Keycloak environment. The resource property must point to the client created in the previous step. This file is used by the client Hawtio JavaScript application side.
Create the keycloak-hawtio. Change the realm and auth-server-url properties according to your Keycloak environment. Start JBoss Fuse 6. The commands in Karaf terminal are similar to this example:. Note that the user needs to have the proper realm role to successfully authenticate to Hawtio. It is assumed that:. Copy the hawtio-wildfly For more details about deploying Hawtio see the Fuse Hawtio documentation. Copy the keycloak-hawtio.